This article provides a solution to an issue in which you are not able to connect to a virtual machine (VM) using RDP with error: CredSSP encryption oracle remediation.
Original product version: Virtual Machine running Windows
Original KB number: 4295591 .
How to verify that the CredSSP update is installed
Check the update history for the following updates, or check the version of TSpkg.dll.
| Operating system | TSpkg.dll version with CredSSP update | CredSSP update |
|---|---|---|
| Windows 7 Service Pack 1 / Windows Server 2008 R2 Service Pack 1 | 6.1.7601.24117 | KB4103718 (Monthly Rollup) |
| KB4103712 (Security-only update) | ||
| Windows Server 2012 | 6.2.9200.22432 | KB4103730 (Monthly Rollup) |
| KB4103726 (Security-only update) | ||
| Windows 8.1 / Windows Server 2012 R2 | 6.3.9600.18999 | KB4103725 (Monthly Rollup) |
| KB4103715 (Security-only update) | ||
| RS1 – Windows 10 Version 1607 / Windows Server 2016 | 10.0.14393.2248 | KB4103723 |
| RS2 – Windows 10 Version 1703 | 10.0.15063.1088 | KB4103731 |
| RS3 – Windows 10 1709 | 10.0.16299.431 | KB4103727 |
Cause
This error occurs if you are trying to establish an insecure RDP connection, and the insecure RDP connection is blocked by an Encryption Oracle Remediation policy setting on the server or client. This setting defines how to build an RDP session by using CredSSP, and whether an insecure RDP is allowed.
See the following interoperability matrix for scenarios that are either vulnerable to this exploit or cause operational failures.
| – | – | Server | – | – | – |
|---|---|---|---|---|---|
| – | – | Updated | Force updated clients | Mitigated | Vulnerable |
| Client | Updated | Allowed | Blocked 2 | Allowed | Allowed |
| Force updated clients | Blocked | Allowed | Allowed | Allowed | |
| Mitigated | Blocked 1 | Allowed | Allowed | Allowed | |
| Vulnerable | Allowed | Allowed | Allowed | Allowed |
Examples
1 The client has the CredSSP update installed, and Encryption Oracle Remediation is set to Mitigated. This client will not RDP to a server that does not have the CredSSP update installed.
2 The server has the CredSSP update installed, and Encryption Oracle Remediation is set to Force updated clients. The server will block any RDP connection from clients that do not have the CredSSP update installed.
Resolution
To resolve the issue, install CredSSP updates for both client and server so that RDP can be established in a secure manner. For more information, see CVE-2018-0886 | CredSSP Remote Code Execution Vulnerability.
How to install this update by using Azure Serial console
-
Sign in to the Azure portal, select Virtual Machine, and then select the VM.
-
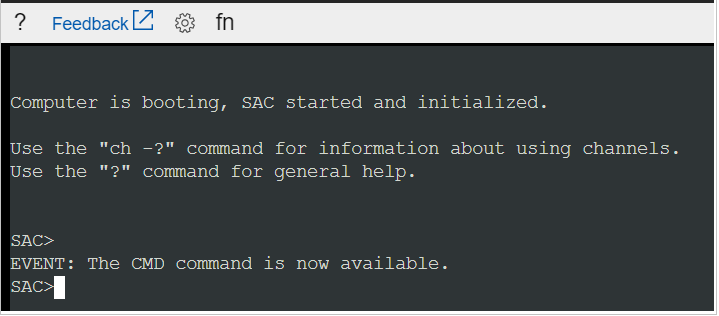
Scroll down to the Support + Troubleshooting section, and then click Serial console (Preview). The serial console requires Special Administrative Console (SAC) to be enabled within the Windows VM. If you do not see SAC> in the console (as shown in the following screenshot), go to the “How to install this update by using Remote PowerShell” section in this article.
-
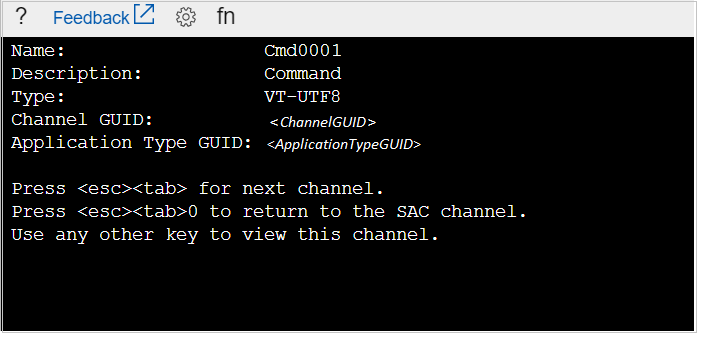
Type
cmdto start a channel that has a CMD instance. -
Type
ch-si 1to switch to the channel that is running the CMD instance. You receive the following output: -
Press Enter, and then enter your login credentials that have administrative permission.
-
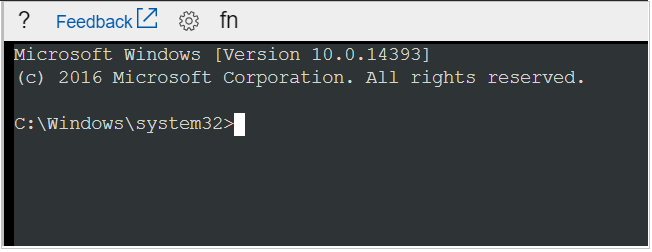
After you enter valid credentials, the CMD instance opens, and you will see the command at which you can start troubleshooting.
-
To start a PowerShell instance, type
PowerShell. -
In the PowerShell instance, run the Serial console script based on the VM operating system. This script performs the following steps:
- Create a folder in which to save the download file.
- Download the update.
- Install the update.
- Add the vulnerability key to allow non-updated clients to connect to the VM.
- Restart the VM
How to install this update by using Remote PowerShell
-
On any Windows-based computer that has PowerShell installed, add the IP address of the VM to the “trusted” list in the host file, as follows:
PowerShellSet-item wsman:\localhost\Client\TrustedHosts -value <IP> -
In the Azure portal, configure Network Security Groups on the VM to allow traffic to port 5986.
-
In the Azure portal, select Virtual Machine > < your VM >, scroll down to the OPERATIONS section, click the Run command, and then run EnableRemotePS.
-
On the Windows-based computer, run the Remote PowerShell script for the appropriate system version of your VM. This script performs the following steps:
- Connect to Remote PowerShell on the VM.
- Create a folder to which to save the download file.
- Download the Credssp update.
- Install the update.
- Set the vulnerability registry key to allow non-updated clients to connect to the VM.
- Enable Serial Console for future and easier mitigation.
- Restart the VM.
Fixed: RDP “This could be due to CredSSP encryption oracle…” Encryption Oracle Remediation
In March 2018, Microsoft released a security update regarding the Credential Security Support Provider protocol (CredSSP) used by the Remote Desktop Protocol (RDP) connection between the Windows Client and Windows Server.
Fixed: RDP “This could be due to CredSSP encryption oracle…”
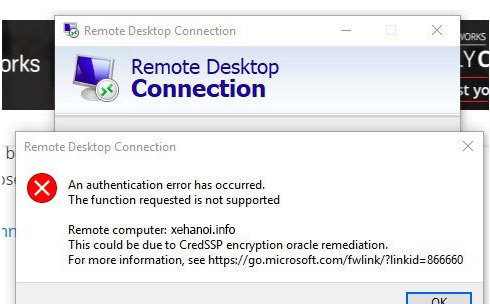
Invisibly this affects the Windows Remote Desktop application. When you open the Remote Desktop client to connect to a Windows Server or VPS you may encounter an error message about ‘CredSSP encryption oracle remediation error’ as shown below when trying to connect Remote Desktop to Windows Server:
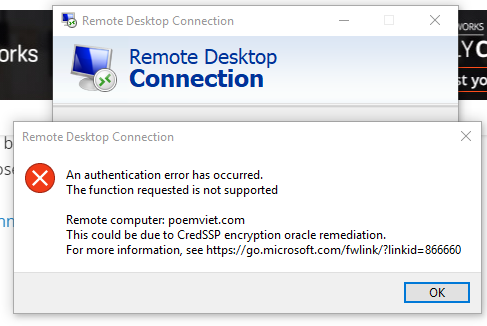
An authentication error has occurred. The function requested is not supported Remote computer: XXX.XXX.XXX.XXX This could be due to CredSSP encryption oracle remediation. For more information, see https://go.microsoft.com/fwlink/?linkid=866660
Before, when this update was not available, it was easy for you to connect to a Windows server using RDP, but after Microsoft forced Windows Server to update a new patch, it was not easy for the client to connect to RDP Windows Server anymore. This situation occurs when an RDP connection is created between a party that has been patched (usually RDP Client) and a party that has not been patched (usually Windows Server).
Reason This could be due to CredSSP encryption oracle
This is due to security vulnerability CVE-2018-0886 | CredSSP Remote Code Execution Vulnerability. In March 2018 Microsoft released an update to address two issues:
Changed the way the CredSSP protocol authenticates requests during authentication.
Change the “Encryption Oracle Remediation” policy configuration from Vulnerable to Mitigated .
RDP authentication problems can arise when the local client and the remote Windows Server server differ in the “Encryption Oracle Remediation” configuration parameter that defines how to build an RDP session with CredSSP.
So there will be 3 cases as follows:
If the client side has automatically updated the patch, and makes an RDP connection to the Windows Server that has not been updated with the patch, the connection will be locked and the error will be displayed as above.
If the client side has not been patched, while Windows Server has updated the patch, RDP will still work. It’s just that the session is vulnerable.
If both the client side and windows server have updated the patch, then the RDP connection is completely secure with the new standard.
Handling InstructionsThis could be due to CredSSP encryption oracle
The best way to handle it is to update the new patch related to CredSSP on Windows Server and RDP Client. But if you want to be able to connect Remote Desktop to a Windows Server server that has not updated the CredSSP vulnerability patch, then on the Windows Client computer you can use the policy to lower the application protection level (policy). ) ‘Encryption Oracle Remediation’ downgrades to ‘Vulnerable’ through Group Policy.
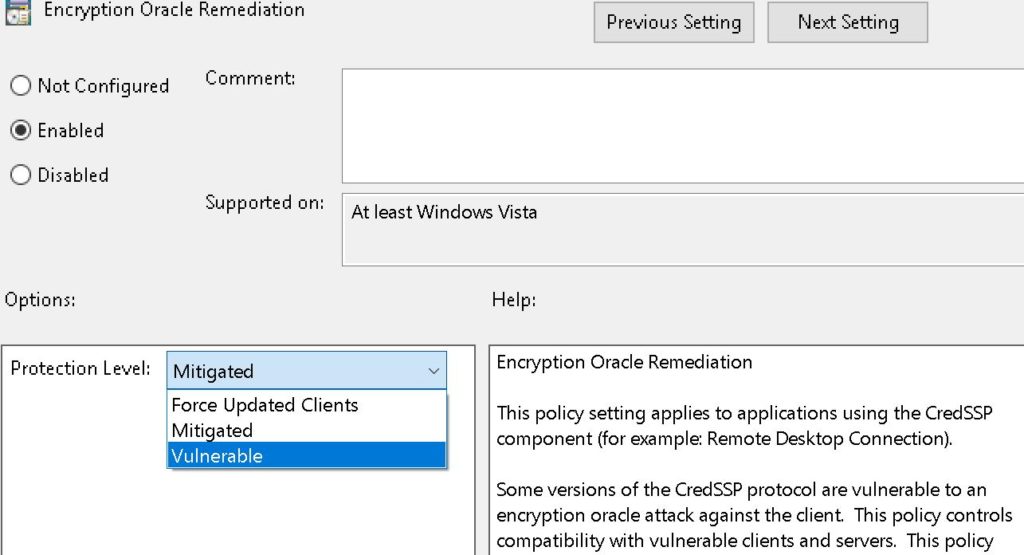
Step 1:
– Open Local Group Policy Editor: type gpedit.msc into Start Menu
Step 2:
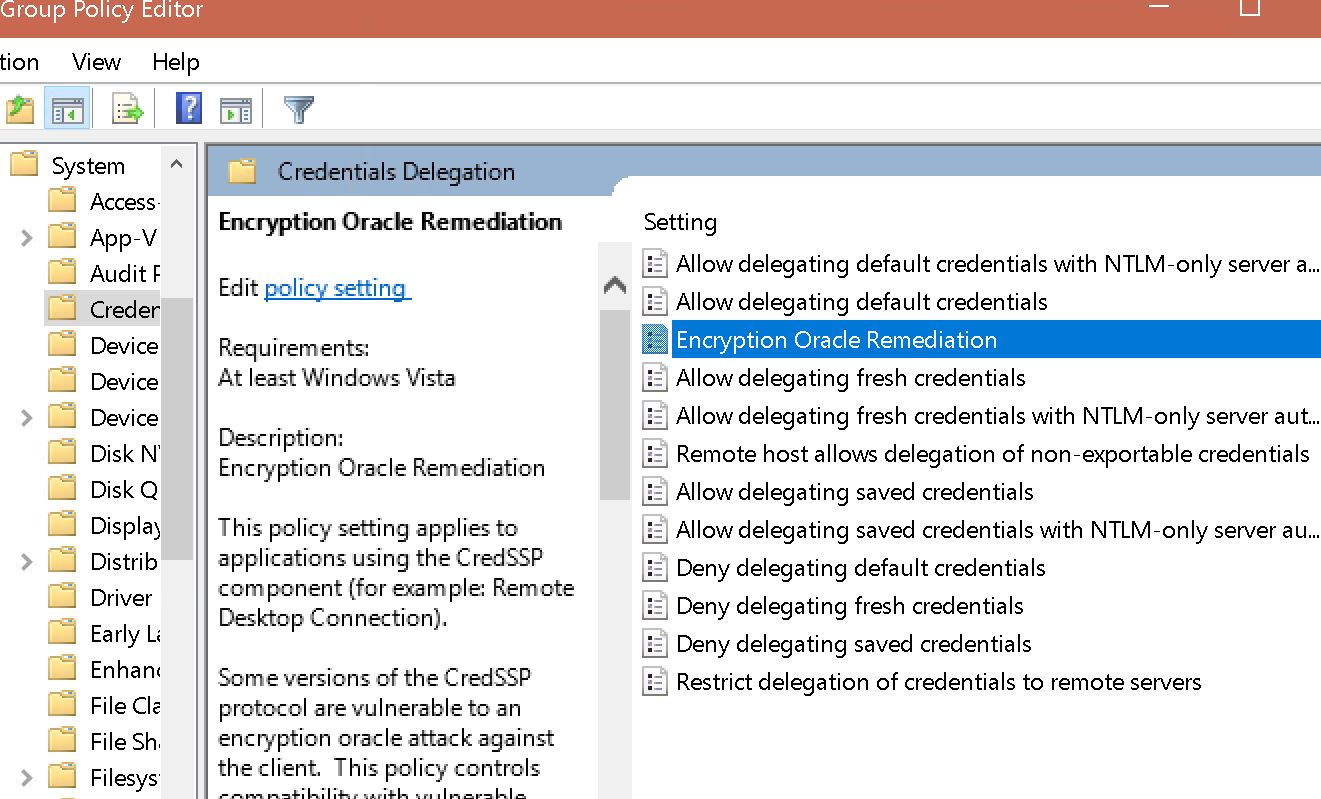
– Move to the policy path as follows: Computer Configuration > Administrative Templates > System > Credentials Delegation
– Click to configure the ‘Encryption Oracle Remediation’ policy.
Step 3:
– Enable ‘Enabled‘.
– Set ‘Protection Level’ to ‘Vulnerable’.
This could be due to CredSSP encryption oracle remediation Windows Server 2012,
This could be due to CredSSP encryption oracle remediation khi Remote Desktop,
This could be due to credssp encryption oracle remediation youtube,
encryption oracle remediation,
Encryption Oracle Remediation missing from group policy,
Encryption oracle remediation not found Windows Servecredssp rdp,
credssp windows 10 home,
credssp regedit,
lỗi credssp,
this could be due to credssp encryption oracle remediation,
credssp encryption oracle remediation,
credssp powershell,
credssp patchr,